All Stories
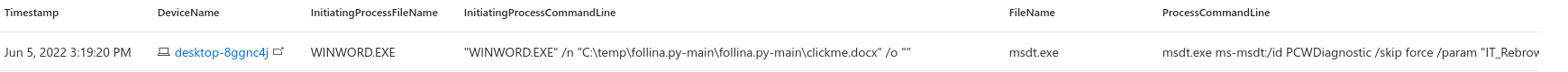
Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022AMSI bypass detection with MDE
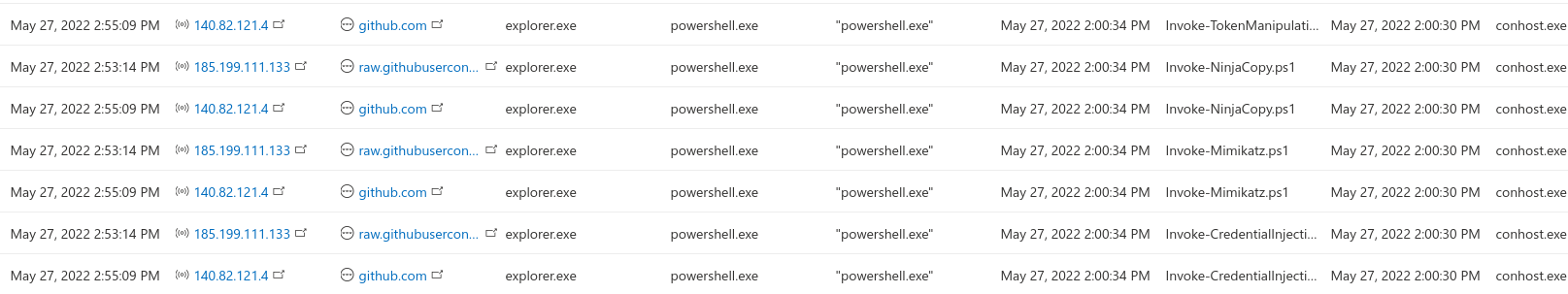
Microsoft has developed AMSI to detect malicious content to be launched by Powershell. The AMSI.dll is injected to the process memory after which the Antivirus programs can use the AP...
In threat hunting, May 27, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
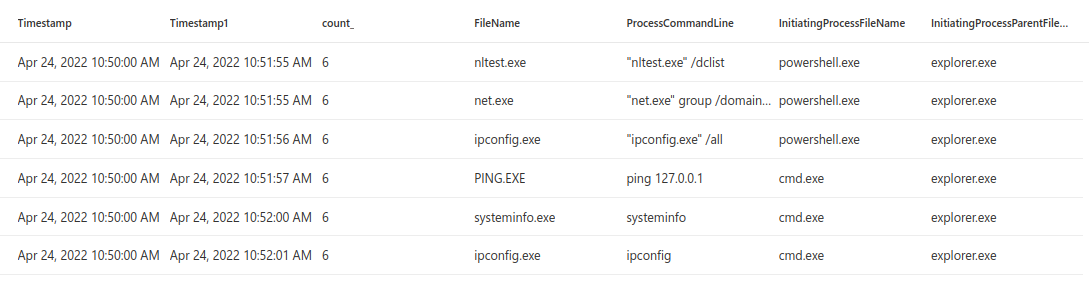
In threat hunting, May 08, 2022Running multiple instances of discovery commands in short period of time
When the attackers have been able to gain initial access to the environment they are often running different kind of commands to gain further information of the environment. The comma...
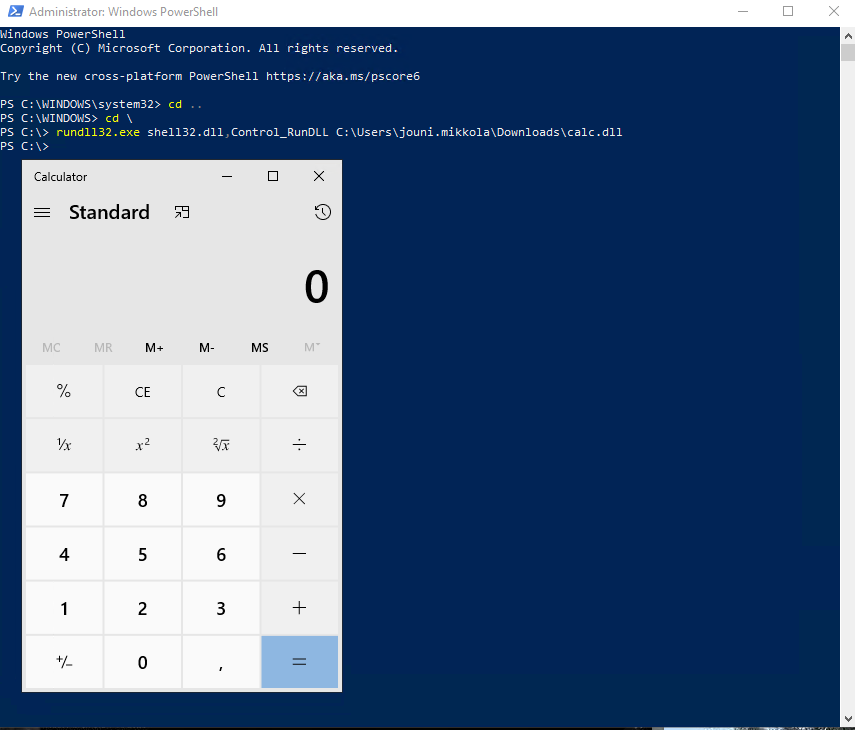
In threat hunting, Apr 30, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
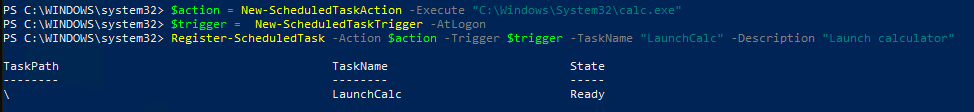
In threat hunting, Apr 20, 2022(Trying to) hunt for a hidden scheduled task
Microsoft DART released an article yesterday of how the malware known as Tarrask has been using scheduled tasks for defense evasion. This malware has been in use by an APT group known...
In threat hunting, Apr 13, 2022How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022Featured
-
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
In threat hunting, -
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, -
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, -
OpenCTI RSS feed support
In threat intelligence, -
Threat Intelligence Platform - OpenCTI
In threat intelligence,