All Stories
MDE/MDI/MDO365 advanced hunt queries to ELK
I’ve been using Jupyter Notebook for quite sometime in threat hunting and incident response purposes. It is great as it offers the python data analytic tools to be used with the data ...
In threat hunting, Nov 28, 2022My version of a home lab
This time I am going to introduced my version of a home lab. This is not as “pro” as many others have but have a good combination of lab and a home computer in a same package. The pos...
In threat hunting, Nov 19, 2022Recent phishing emails + Emotet recent sample analysis
Phishing emails
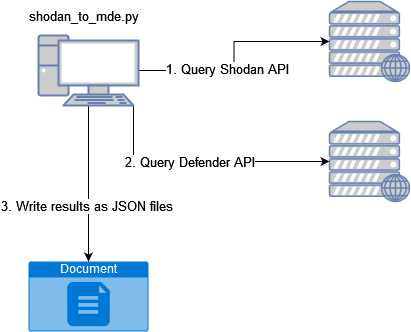
In threat hunting, Nov 13, 2022From Shodan to MDE queries
I’ve had an idea for some time for using the Shodan and MDE API:s. The idea is to pull recently identified C2 servers from Shodan and use the IP-addresses to run a query against the M...
In threat hunting, Sep 04, 2022Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
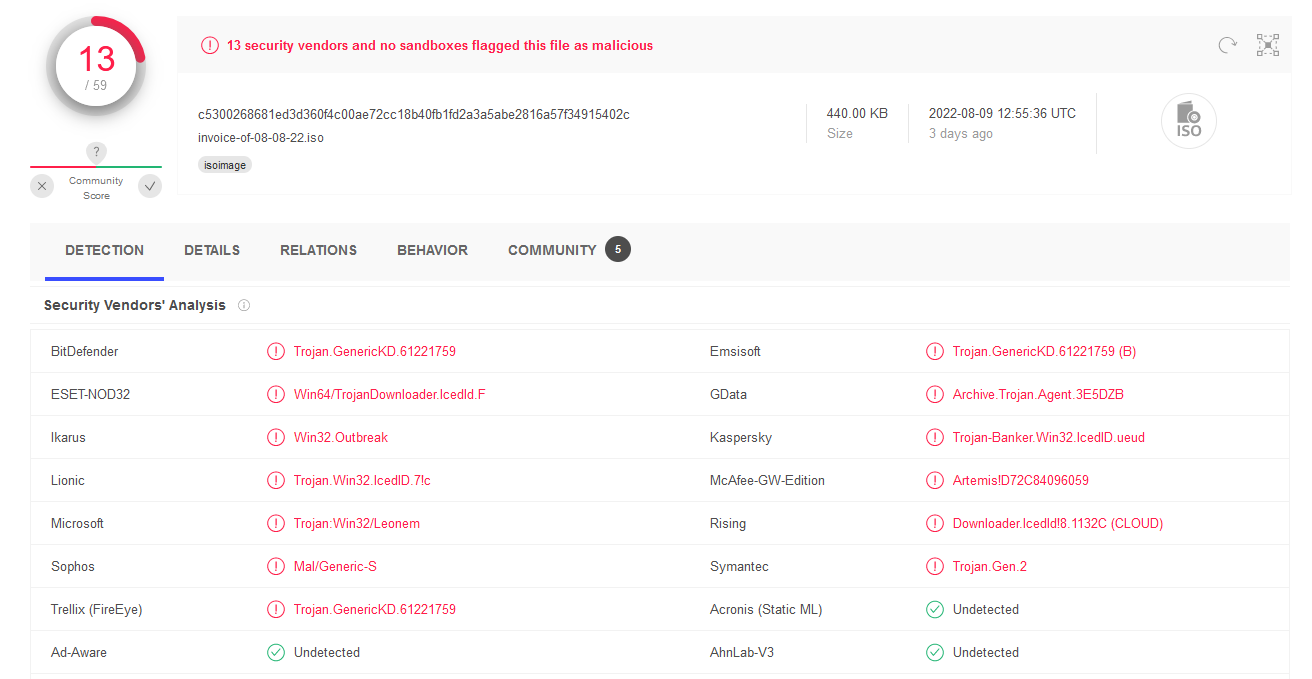
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
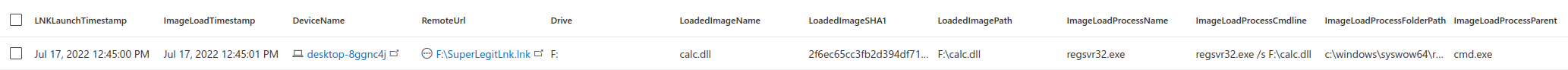
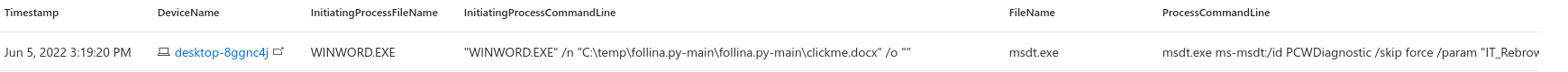
In threat hunting, Jul 17, 2022Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022Featured
-
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, -
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, -
Having a look at a few new fields in MDE
In threat hunting, -
OpenCTI RSS feed support
In threat intelligence, -
Threat Intelligence Platform - OpenCTI
In threat intelligence,