Tags
crowdstrike
How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022defender for endpoint
Exploring hunting options for catching Impacket
Hunting for usage of Impacket
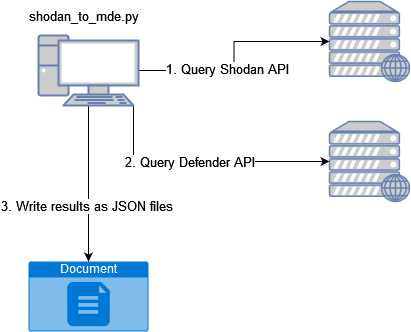
In threat hunting, Apr 13, 2024From Shodan to MDE queries
I’ve had an idea for some time for using the Shodan and MDE API:s. The idea is to pull recently identified C2 servers from Shodan and use the IP-addresses to run a query against the M...
In threat hunting, Sep 04, 2022Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
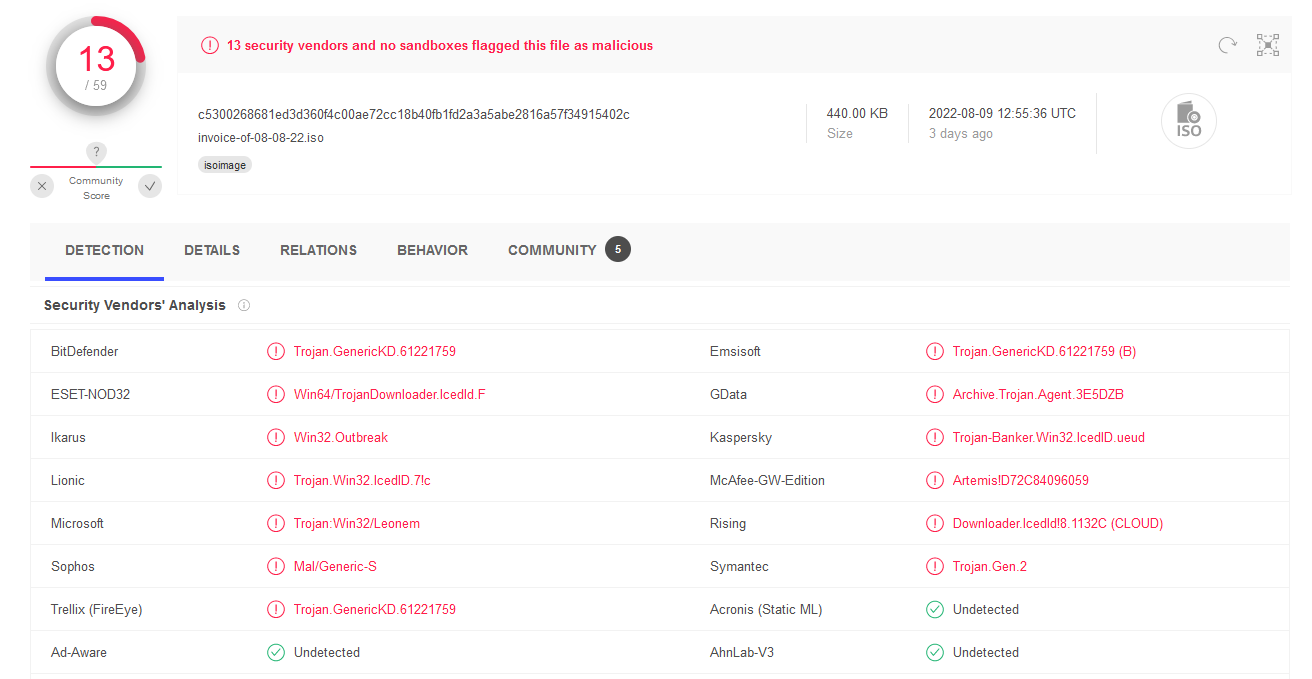
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
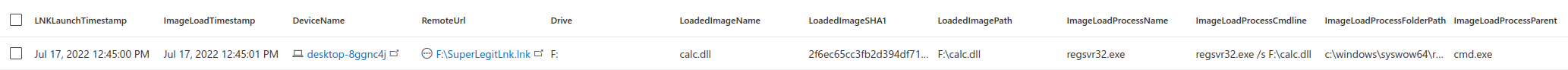
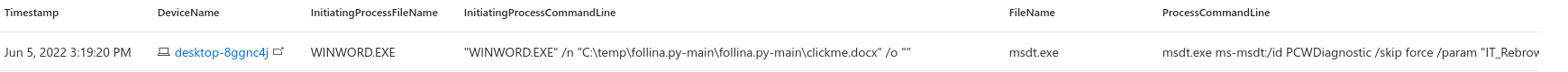
In threat hunting, Jul 17, 2022Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022AMSI bypass detection with MDE
Microsoft has developed AMSI to detect malicious content to be launched by Powershell. The AMSI.dll is injected to the process memory after which the Antivirus programs can use the AP...
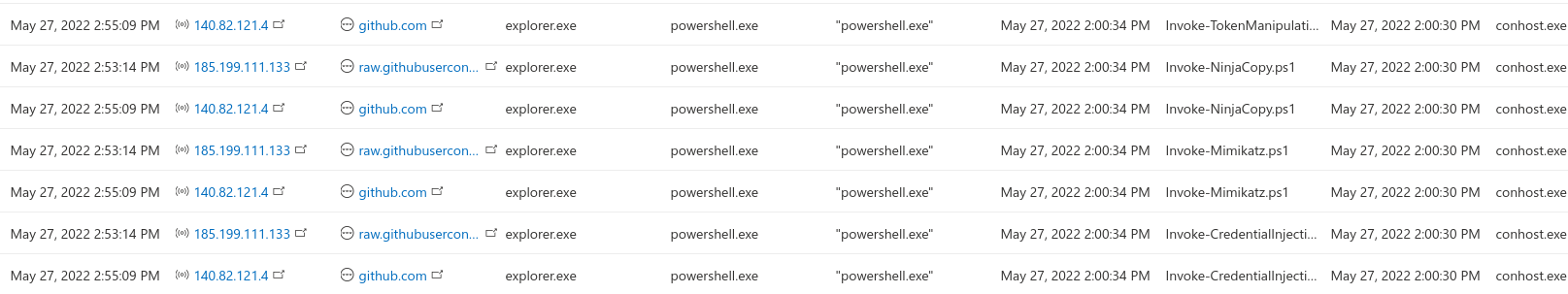
In threat hunting, May 27, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
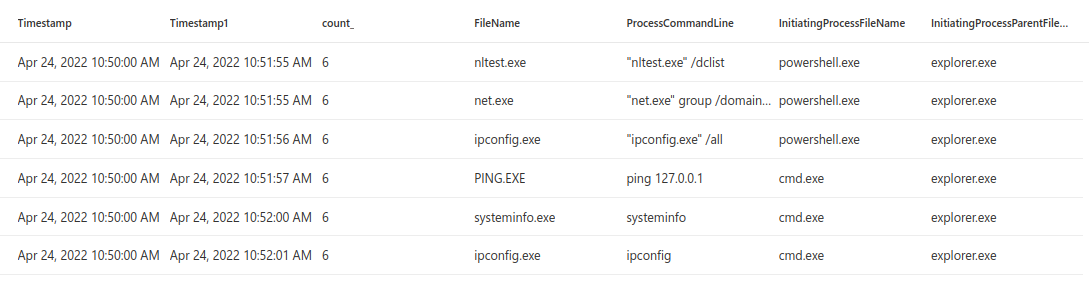
In threat hunting, May 08, 2022Running multiple instances of discovery commands in short period of time
When the attackers have been able to gain initial access to the environment they are often running different kind of commands to gain further information of the environment. The comma...
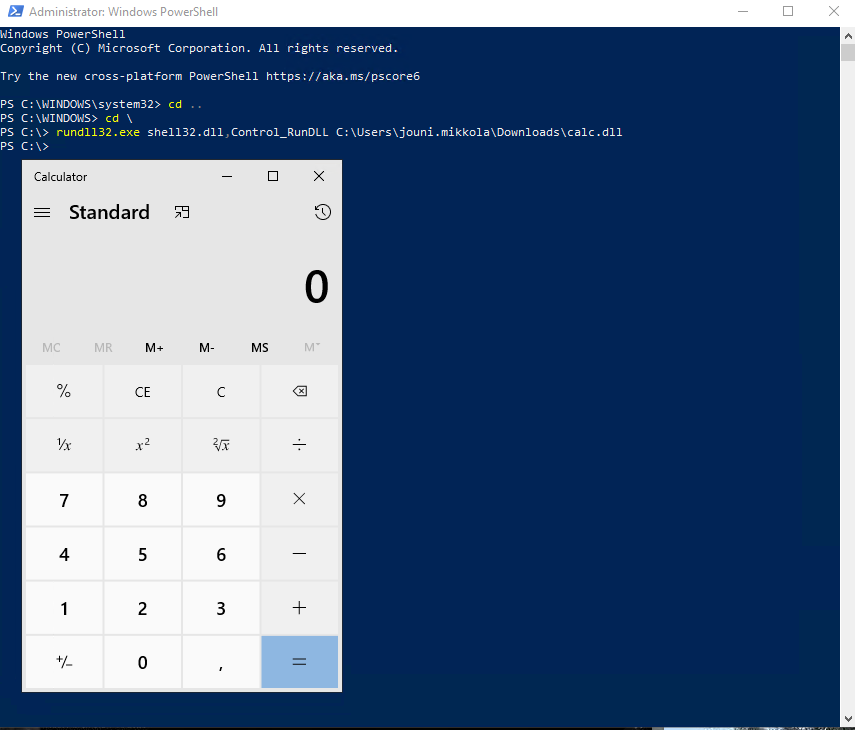
In threat hunting, Apr 30, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
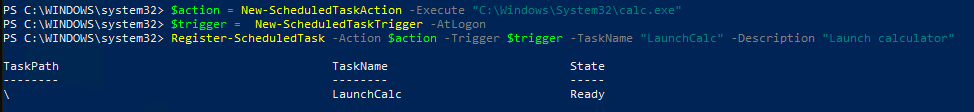
In threat hunting, Apr 20, 2022(Trying to) hunt for a hidden scheduled task
Microsoft DART released an article yesterday of how the malware known as Tarrask has been using scheduled tasks for defense evasion. This malware has been in use by an APT group known...
In threat hunting, Apr 13, 2022How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022kql
Having a look at a few new fields in MDE
Having a look at a few new fields in MDEI noticed that there has been a few new fields added to the Advanced hunt tables. These fields can be useful for threat hunting and incident re...
In threat hunting, Feb 28, 2025Look into couple of suspicous registry activities
Look into couple of suspicous registry activities
In threat hunting, Feb 08, 2025Hunting for Windows Subsystem for Linux based attacks
Hunting for WSL based Badness
In threat hunting, Nov 10, 2024Exploring hunting options for catching Impacket
Hunting for usage of Impacket
In threat hunting, Apr 13, 2024Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022AMSI bypass detection with MDE
Microsoft has developed AMSI to detect malicious content to be launched by Powershell. The AMSI.dll is injected to the process memory after which the Antivirus programs can use the AP...
In threat hunting, May 27, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
In threat hunting, May 08, 2022Running multiple instances of discovery commands in short period of time
When the attackers have been able to gain initial access to the environment they are often running different kind of commands to gain further information of the environment. The comma...
In threat hunting, Apr 30, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
In threat hunting, Apr 20, 2022(Trying to) hunt for a hidden scheduled task
Microsoft DART released an article yesterday of how the malware known as Tarrask has been using scheduled tasks for defense evasion. This malware has been in use by an APT group known...
In threat hunting, Apr 13, 2022How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022mde
Having a look at a few new fields in MDE
Having a look at a few new fields in MDEI noticed that there has been a few new fields added to the Advanced hunt tables. These fields can be useful for threat hunting and incident re...
In threat hunting, Feb 28, 2025Look into couple of suspicous registry activities
Look into couple of suspicous registry activities
In threat hunting, Feb 08, 2025Hunting for Windows Subsystem for Linux based attacks
Hunting for WSL based Badness
In threat hunting, Nov 10, 2024MDE/MDI/MDO365 advanced hunt queries to ELK
I’ve been using Jupyter Notebook for quite sometime in threat hunting and incident response purposes. It is great as it offers the python data analytic tools to be used with the data ...
In threat hunting, Nov 28, 2022Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022AMSI bypass detection with MDE
Microsoft has developed AMSI to detect malicious content to be launched by Powershell. The AMSI.dll is injected to the process memory after which the Antivirus programs can use the AP...
In threat hunting, May 27, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
In threat hunting, May 08, 2022Running multiple instances of discovery commands in short period of time
When the attackers have been able to gain initial access to the environment they are often running different kind of commands to gain further information of the environment. The comma...
In threat hunting, Apr 30, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
In threat hunting, Apr 20, 2022(Trying to) hunt for a hidden scheduled task
Microsoft DART released an article yesterday of how the malware known as Tarrask has been using scheduled tasks for defense evasion. This malware has been in use by an APT group known...
In threat hunting, Apr 13, 2022How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022spl
How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022threat hunting
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
In threat hunting, Feb 24, 2026Having a look at a few new fields in MDE
Having a look at a few new fields in MDEI noticed that there has been a few new fields added to the Advanced hunt tables. These fields can be useful for threat hunting and incident re...
In threat hunting, Feb 28, 2025Look into couple of suspicous registry activities
Look into couple of suspicous registry activities
In threat hunting, Feb 08, 2025Hunting for Windows Subsystem for Linux based attacks
Hunting for WSL based Badness
In threat hunting, Nov 10, 2024Exploring hunting options for catching Impacket
Hunting for usage of Impacket
In threat hunting, Apr 13, 2024Malware statistics to ELK
I’ve been somewhat busy lately and hadn’t had much time to write anything to the blog unfortunately. I also have had some issues in thinking of good topics as I don’t want to get stuc...
In threat hunting, Feb 16, 2023MDE/MDI/MDO365 advanced hunt queries to ELK
I’ve been using Jupyter Notebook for quite sometime in threat hunting and incident response purposes. It is great as it offers the python data analytic tools to be used with the data ...
In threat hunting, Nov 28, 2022Recent phishing emails + Emotet recent sample analysis
Phishing emails
In threat hunting, Nov 13, 2022Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022AMSI bypass detection with MDE
Microsoft has developed AMSI to detect malicious content to be launched by Powershell. The AMSI.dll is injected to the process memory after which the Antivirus programs can use the AP...
In threat hunting, May 27, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
In threat hunting, May 08, 2022Running multiple instances of discovery commands in short period of time
When the attackers have been able to gain initial access to the environment they are often running different kind of commands to gain further information of the environment. The comma...
In threat hunting, Apr 30, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
In threat hunting, Apr 20, 2022(Trying to) hunt for a hidden scheduled task
Microsoft DART released an article yesterday of how the malware known as Tarrask has been using scheduled tasks for defense evasion. This malware has been in use by an APT group known...
In threat hunting, Apr 13, 2022How to start with host based threat hunting?
How to start with host based threat hunting?
In threat hunting, Apr 10, 2022scheduled tasks
(Trying to) hunt for a hidden scheduled task
Microsoft DART released an article yesterday of how the malware known as Tarrask has been using scheduled tasks for defense evasion. This malware has been in use by an APT group known...
In threat hunting, Apr 13, 2022dll loads
Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
In threat hunting, May 08, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
In threat hunting, Apr 20, 2022rundll32
Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
In threat hunting, May 08, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
In threat hunting, Apr 20, 2022regsvr32
Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022DLL image loads from suspicious locations by regsvr32.exe / rundll32.exe
DLL images are being used quite a lot by the attackers to load their malicious code. I’ve done several different queries that are targeting this attack technique. I have been having a...
In threat hunting, Apr 20, 2022bumblebee
Bzz.. Bzz.. Bumblebee loader
Quite recently, a new loader has been popping up. This loader is likely been developed to counter the Microsoft’s change to the macro behavior, as the macros will be disabled on the d...
In threat hunting, May 08, 2022AMSI bypass
AMSI bypass detection with MDE
Microsoft has developed AMSI to detect malicious content to be launched by Powershell. The AMSI.dll is injected to the process memory after which the Antivirus programs can use the AP...
In threat hunting, May 27, 2022follina
Detecting Follina with MDE
About a week ago there was a new zero-day office “zero-click” vulnerability noted. This vulnerability was dubbed as Follina by Kevin Beaumont who discovered it while investigating a d...
In threat hunting, Jun 05, 2022ISO
Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022Detecting a Payload delivered with ISO files with MDE
It’s been a little quiet on my blog for a while now - reason being that I was on a holiday and rather did other things than sit in front of a computer. Just got back and have some fre...
In threat hunting, Jul 17, 2022malware
Malware statistics to ELK
I’ve been somewhat busy lately and hadn’t had much time to write anything to the blog unfortunately. I also have had some issues in thinking of good topics as I don’t want to get stuc...
In threat hunting, Feb 16, 2023Running live malware for threat hunting purposes
This time I am trying something different. I am in no way, shape or form capable in malware analysis but I was thinking if it could be useful to run a live malware on a device with MD...
In threat hunting, Aug 13, 2022shodan
From Shodan to MDE queries
I’ve had an idea for some time for using the Shodan and MDE API:s. The idea is to pull recently identified C2 servers from Shodan and use the IP-addresses to run a query against the M...
In threat hunting, Sep 04, 2022emotet
Recent phishing emails + Emotet recent sample analysis
Phishing emails
In threat hunting, Nov 13, 2022phishing
Recent phishing emails + Emotet recent sample analysis
Phishing emails
In threat hunting, Nov 13, 2022sysmon
Recent phishing emails + Emotet recent sample analysis
Phishing emails
In threat hunting, Nov 13, 2022splunk
Recent phishing emails + Emotet recent sample analysis
Phishing emails
In threat hunting, Nov 13, 2022detection lab
My version of a home lab
This time I am going to introduced my version of a home lab. This is not as “pro” as many others have but have a good combination of lab and a home computer in a same package. The pos...
In threat hunting, Nov 19, 2022homelab
My version of a home lab
This time I am going to introduced my version of a home lab. This is not as “pro” as many others have but have a good combination of lab and a home computer in a same package. The pos...
In threat hunting, Nov 19, 2022qakbot
elk
Malware statistics to ELK
I’ve been somewhat busy lately and hadn’t had much time to write anything to the blog unfortunately. I also have had some issues in thinking of good topics as I don’t want to get stuc...
In threat hunting, Feb 16, 2023MDE/MDI/MDO365 advanced hunt queries to ELK
I’ve been using Jupyter Notebook for quite sometime in threat hunting and incident response purposes. It is great as it offers the python data analytic tools to be used with the data ...
In threat hunting, Nov 28, 2022elasticsearch
MDE/MDI/MDO365 advanced hunt queries to ELK
I’ve been using Jupyter Notebook for quite sometime in threat hunting and incident response purposes. It is great as it offers the python data analytic tools to be used with the data ...
In threat hunting, Nov 28, 2022kibana
MDE/MDI/MDO365 advanced hunt queries to ELK
I’ve been using Jupyter Notebook for quite sometime in threat hunting and incident response purposes. It is great as it offers the python data analytic tools to be used with the data ...
In threat hunting, Nov 28, 2022html smuggling
qbot
asyncrat
msbuild
statistics
Malware statistics to ELK
I’ve been somewhat busy lately and hadn’t had much time to write anything to the blog unfortunately. I also have had some issues in thinking of good topics as I don’t want to get stuc...
In threat hunting, Feb 16, 2023turla
opencti
threat intelligence
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, Nov 30, 2025Scattered Spider: When Social Engineering Meets Supply Chain Risk
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, Jun 21, 2025featured
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
In threat hunting, Feb 24, 2026TI Dashboar: AI generated Cyber Threat Intelligence dashboard
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, Nov 30, 2025Scattered Spider: When Social Engineering Meets Supply Chain Risk
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, Jun 21, 2025persistence
service
SEO poisoning
credential dumping
impacket
Exploring hunting options for catching Impacket
Hunting for usage of Impacket
In threat hunting, Apr 13, 2024dfir
The DFIR thing reg parsing #1
This blog post was lost in migration from Wordpress to Github Pages. :(
In dfir, Aug 29, 2024ir
The DFIR thing reg parsing #1
This blog post was lost in migration from Wordpress to Github Pages. :(
In dfir, Aug 29, 2024dfir thing
The DFIR thing reg parsing #1
This blog post was lost in migration from Wordpress to Github Pages. :(
In dfir, Aug 29, 2024evtx
The DFIR thing reg parsing #1
This blog post was lost in migration from Wordpress to Github Pages. :(
In dfir, Aug 29, 2024chainsaw
The DFIR thing reg parsing #1
This blog post was lost in migration from Wordpress to Github Pages. :(
In dfir, Aug 29, 2024hayabusa
The DFIR thing reg parsing #1
This blog post was lost in migration from Wordpress to Github Pages. :(
In dfir, Aug 29, 2024wsl
Hunting for Windows Subsystem for Linux based attacks
Hunting for WSL based Badness
In threat hunting, Nov 10, 2024sticky
Hunting for Windows Subsystem for Linux based attacks
Hunting for WSL based Badness
In threat hunting, Nov 10, 2024scattered spider
Scattered Spider: When Social Engineering Meets Supply Chain Risk
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, Jun 21, 2025incident preparation
Scattered Spider: When Social Engineering Meets Supply Chain Risk
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, Jun 21, 2025ti dashboar
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, Nov 30, 2025Featured
-
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
In threat hunting, -
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, -
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, -
OpenCTI RSS feed support
In threat intelligence, -
Threat Intelligence Platform - OpenCTI
In threat intelligence,