All Stories
Exploring hunting options for catching Impacket
Hunting for usage of Impacket
In threat hunting, Apr 13, 2024Malware statistics to ELK
I’ve been somewhat busy lately and hadn’t had much time to write anything to the blog unfortunately. I also have had some issues in thinking of good topics as I don’t want to get stuc...
In threat hunting, Feb 16, 2023Featured
-
Why Your Threat Hunting Program Is Working (Even When It Finds Nothing)
In threat hunting, -
TI Dashboar: AI generated Cyber Threat Intelligence dashboard
In threat intelligence, -
Scattered Spider: When Social Engineering Meets Supply Chain Risk
In incident preparation, -
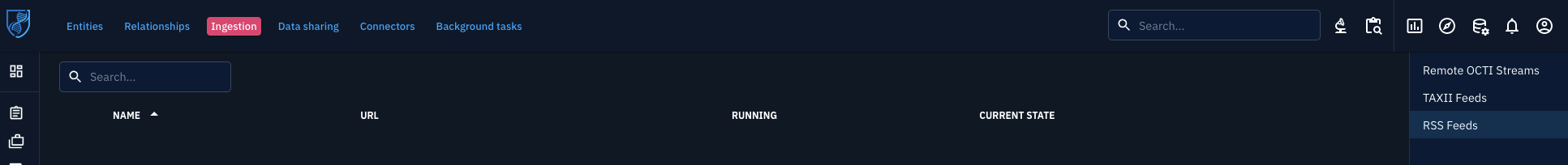
OpenCTI RSS feed support
In threat intelligence, -
Threat Intelligence Platform - OpenCTI
In threat intelligence,